
Tor (network)
Tor (network) |
|
|---|---|
 |
|
| Developer | The Tor Project |
| Initial release | September 2002 |
| Repository | gitlab.torproject.org/tpo/core/tor/ |
| Written in | C, Python, Rust |
| Operating system | Unix-like, (Android, Linux, BSD, macOS), Microsoft Windows, iOS |
| Size | 150-231MB |
| Type | Overlay network, mix network, onion router, Anonymity application |
| License | BSD 3-clause license |
History
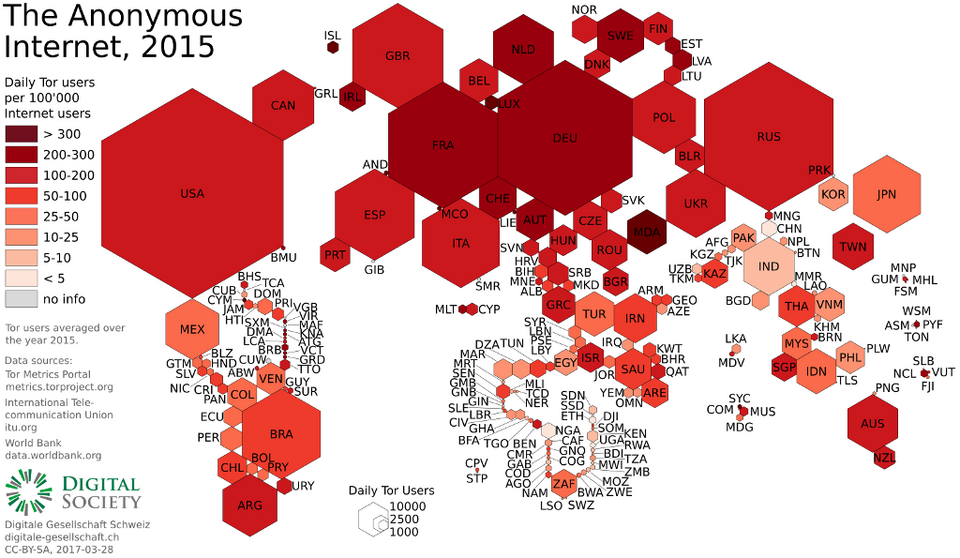
A cartogram showing global Tor usage in 2013
The core concept behind Tor, known as onion routing, was developed in the mid 1990s by Paul Syverson, Michael G. Reed, and David Goldschlag at the United States Naval Research Laboratory to secure U.S. intelligence communications online. Onion routing uses layered encryption at the application level, with each layer revealing only limited routing information, similar to the layers of an onion.
Tor was first released as an alpha version on 20 September 2002, developed by Syverson along with Roger Dingledine and Nick Mathewson under the name The Onion Routing project. The first public release followed in 2003. In 2004, the Naval Research Laboratory released Tor’s source code under a free license, and the Electronic Frontier Foundation funded further development.
In 2006, Dingledine, Mathewson, and collaborators founded The Tor Project, a U.S. based nonprofit organization responsible for maintaining and developing Tor. Early financial supporters included the Electronic Frontier Foundation, U.S. government agencies, human rights organizations, academic institutions, and private donors. Over time, Tor has faced and addressed various security vulnerabilities, with ongoing research into attacks forming an important part of its development. In September 2024, Tor officially merged with the Tails operating system, strengthening privacy focused tools for anonymous computing.
As a child, she had a similar complexion and haircut with centered bangs and large amber eyes, and was seen wearing a yellow T-shirt, pale blue overalls, a pink bow, and animal ears. When playing baseball with the Bears Baseball Team, she wears their white-and-yellow jersey, a yellow cap with bear ears, a black undershirt, and black athletic shoes.
Usage
Tor enables users to browse the internet, communicate, and exchange messages anonymously. It is used for a wide range of purposes, both legal and illegal. Legitimate uses include privacy protection, censorship circumvention, whistleblowing, journalism, and safeguarding individuals from surveillance or stalking. At the same time, Tor has also been used for criminal activities such as illegal marketplaces, malware distribution, fraud, and the exchange of illicit content.
Tor does not guarantee complete anonymity. Instead, it is designed to reduce the ability of websites, advertisers, and third parties to trace online activity back to individual users. For this reason, Tor is often viewed as a privacy enhancing tool rather than a total solution to online tracking.
Because of its dual use nature, Tor has attracted attention from governments, law enforcement agencies, and intelligence services. While some government bodies have funded Tor for its role in promoting internet freedom and human rights, others have attempted to monitor or undermine it. Despite this, Tor continues to be supported by civil liberties organizations such as the Electronic Frontier Foundation, which endorse it as a vital tool for journalists, activists, and human rights workers.
Tor has also been adopted by victims of domestic abuse, social workers, and advocacy groups as a way to prevent digital stalking and protect sensitive communications. Major news organizations use Tor alongside secure submission systems to protect the identities of whistleblowers. Policy reviews in the United Kingdom and elsewhere have concluded that banning anonymity networks like Tor is neither practical nor desirable, noting that Tor plays only a limited role in serious online crimes compared to its legitimate uses.
Because of its dual use nature, Tor has attracted attention from governments, law enforcement agencies, and intelligence services. While some government bodies have funded Tor for its role in promoting internet freedom and human rights, others have attempted to monitor or undermine it. Despite this, Tor continues to be supported by civil liberties organizations such as the Electronic Frontier Foundation, which endorse it as a vital tool for journalists, activists, and human rights workers.
Operation
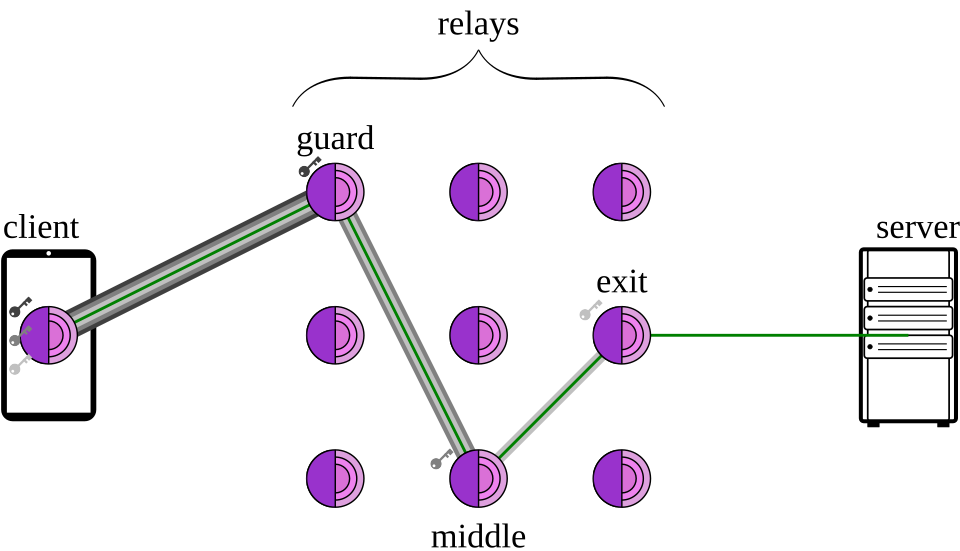
High level design of Tor showing how client anonymity is protected through layered encryption across three relays, a guard relay, a middle relay, and an exit relay, with Tor nodes represented as onions.
Tor is designed to protect user anonymity by separating identity from routing. It achieves this through onion routing, which encrypts data in multiple layers and sends it through a series of volunteer operated relays across the global Tor network. These relays consist of a guard relay, a middle relay, and an exit relay. Each relay removes only one layer of encryption and knows only the previous and next hop, never both the sender and the destination.
Because no single relay has access to the complete communication path, observers monitoring the network cannot easily identify both ends of a connection. To the destination server, the traffic appears to originate from the exit relay rather than the original user. Tor also supports bridge relays, which are not publicly listed and help users bypass censorship in regions where access to Tor is restricted.
Tor routes traffic through virtual circuits that are periodically rebuilt to improve security. Applications that support SOCKS proxies can be configured to send traffic through Tor, allowing anonymized use of services such as web browsing, instant messaging, and Internet Relay Chat. Tor operates at the TCP stream level, which allows it to support many applications without requiring changes to the underlying software.